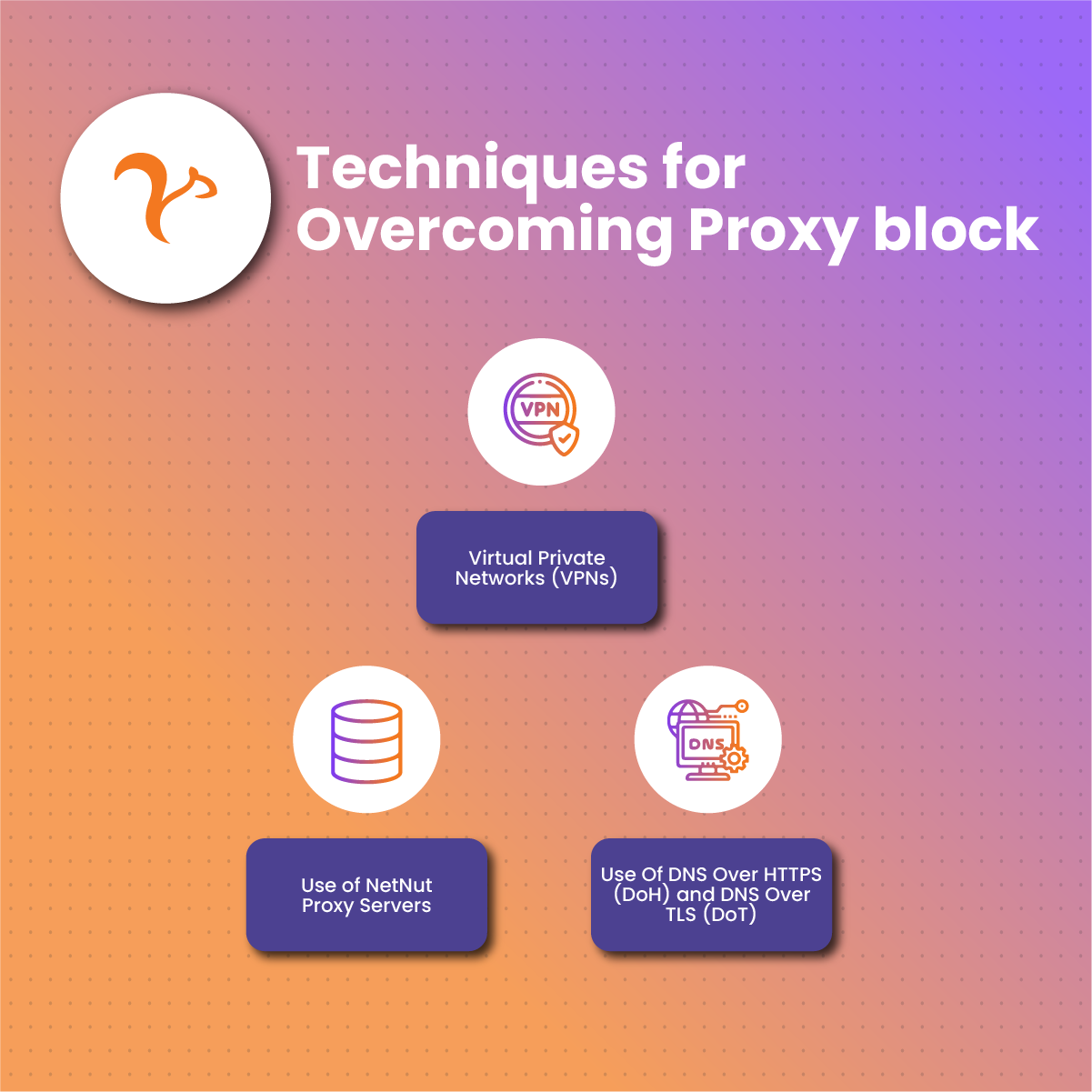
**Web Proxy That Bypasses Any Firewall Without Warning!** How secure access is shifting in a filtered digital world In an era where internet access is increasingly monitored—whether for privacy, education, or work—many users are discovering a quiet but powerful tool: web proxies designed to bypass firewall restrictions without warning. This growing need stems from evolving online behaviors across the U.S., where concerns about censorship, geographic content limits, and network surveillance are reshaping how people connect. The phrase “Web Proxy That Bypasses Any Firewall Without Warning” now defines a practical solution for individuals seeking seamless, alert-free access—whether traveling, working remotely, or exploring sensitive information. As digital boundaries tighten, understanding this technology helps users navigate connectivity challenges with clarity and control. **Why the Demand for Firewall-Aware Proxies Is Growing** In the U.S., remote work, online education, and international collaboration remain mainstream. Yet restrictions at schools, workplaces, and even home networks—often imposed for policy, security, or compliance reasons—create friction. These barriers prompt users to seek reliable tools that allow unobtrusive access. The phrase “Web Proxy That Bypasses Any Firewall Without Warning” surfaces as a key search term because people want to avoid detection, judgment, or disruption. With rising awareness of digital privacy and cybersecurity, more individuals are turning to smarter proxy solutions that blend functionality with stealth. This reflective shift toward proactive, cautious browsing defines today’s digital landscape. **How Does a Web Proxy That Bypasses Any Firewall Without Warning Work?** At its core, a proxy that bypasses firewall restrictions routes your internet traffic through an intermediary server that masks or alters your network signals. Unlike standard proxies requiring manual configuration, this type uses advanced routing techniques—such as encrypted protocols, IP rotation, or protocol obfuscation—to avoid detection. When activated, it appears as a legitimate background connection, requiring no user alert. This seamless handed-off process means users experience minimal latency while circumventing IP blocks, DNS filtering, or content limits. The technology relies on dynamic adaptation, ensuring access remains stable even when network rules change abruptly. **Common Questions About Web Proxy That Bypasses Any Firewall Without Warning!**
**Q: Will I get caught using a frontstation proxy?** A: Many modern firewalls detect simple proxy use, but advanced systems avoid flags through obfuscation. Still, use with awareness and legality. **Q: Can this proxy expose my data?** A: Use trusted tools that support encryption. Leaving connections unsecured risks interception; always choose proxies with secure tunneling protocols. **Q: Are these proxies free, or do I need a subscription?** A: Options range from free, ad-supported services to paid subscriptions offering greater stability, speed, and privacy—ideal for frequent or professional use. **Opportunities and Realistic Expectations** Web proxies that bypass firewalls without warning offer practical benefits: bypassing school or workplace blocks, accessing region-locked research or educational content, and maintaining privacy in high-surveillance zones. However, they aren’t universal solutions. Performance depends on server load, network conditions, and firewall sophistication. Users should manage expectations and view these tools as part of a broader digital strategy, not a guaranteed bypass in all scenarios. **Common Misconceptions Explained** A major concern is that firewalls are easily tricked or disabled—this is false. Mature proxy systems use layered obfuscation and rapid IP switching, making them resilient. Some believe they reveal full identity; in truth, careful proxies route only traffic without exposing personal data. Others worry about malware—legitimate services filter threats by design, minimizing risk. Lastly, many assume stealth means invincibility, but ethics and legality remain key: transparency and responsible use build long-term trust. **Who Benefits From a Web Proxy That Bypasses Any Firewall Without Warning?** This tool serves diverse users across the U.S.: students overcoming internet blocks at school, remote workers accessing global tools behind company firewalls, travelers unlocking region-ablimited resources, and advocates in regions with restricted access. It also appeals to professionals handling sensitive research, journalists navigating restrictive zones, and families managing digital literacy at home. The real value lies not in trickery, but in empowering informed, adaptive connectivity. **Soft CTA: Stay Informed, Remain In Control** Understanding what “Web Proxy That Bypasses Any Firewall Without Warning” truly means helps users navigate today’s complex digital environment with confidence. Whether you’re exploring new learning paths, connecting globally, or safeguarding privacy, choosing the right proxy is about balance—between accessibility, safety, and responsibility. Keep exploring, staying alert, and informed—your digital journey matters.
ZenLeaf: The Simple Herb That Quiets Your Mind When Everything Feels Chaotic
Final Clash Revealed: How Xiaolin Showdown Changed the Future of Martial Arts Gaming
The Hidden Truth Behind XIM Matrix Will Shock Everyone Experiment Goes Wrong in Secret Lab