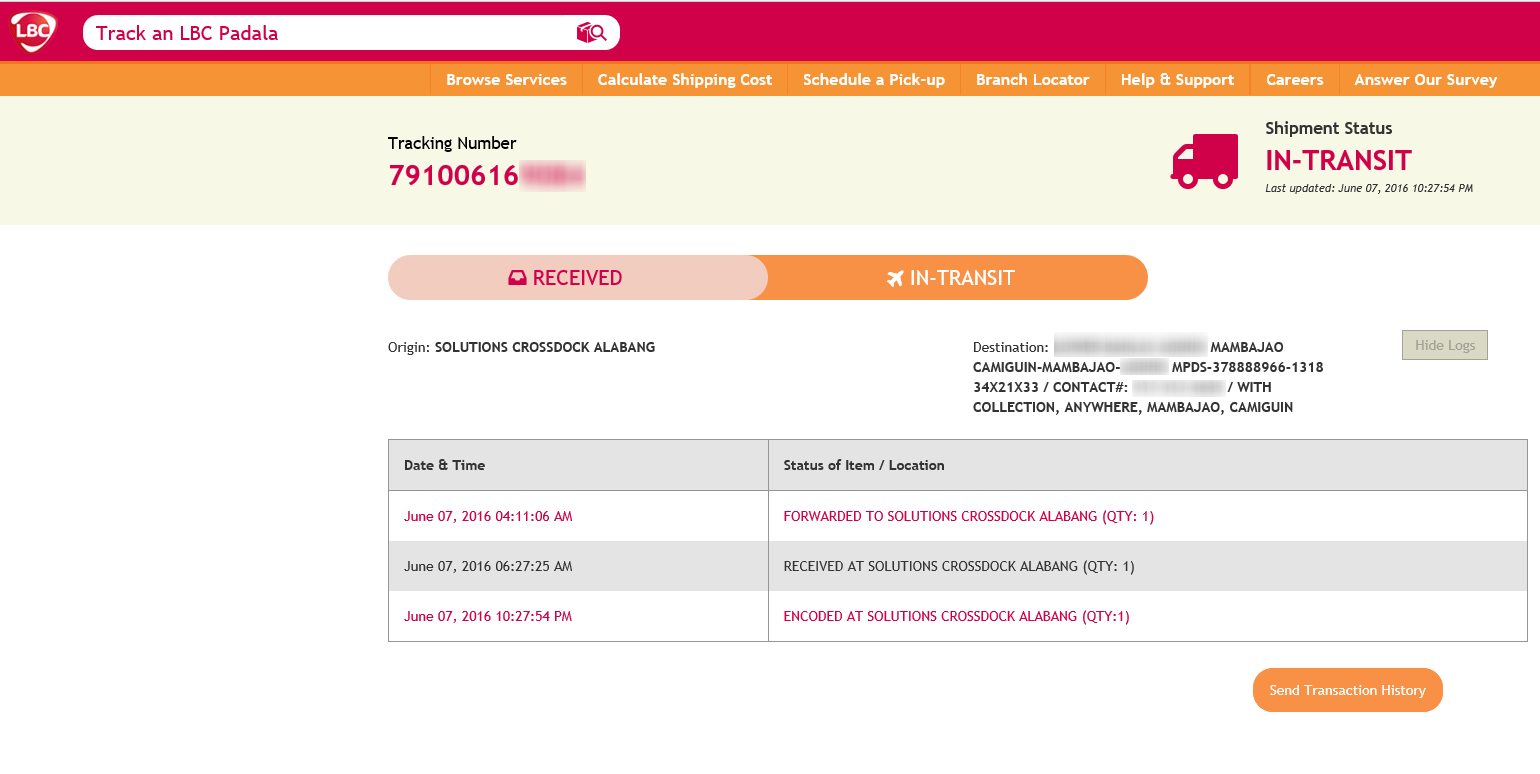
**Watch How LBC Tracking Spoofs Everything You Think You Know — and Why It’s Taking Digital Conversations by Storm** In a digital landscape flooded with claims about identity, privacy, and digital footprints, a growing conversation is unfolding around how LBC tracking tools are being reimagined. The phrase *Watch How LBC Tracking Spoofs Everything You Think You Know* no longer just sparks curiosity—it signals a deeper interest in reclaiming control over personal data and online visibility. More people than ever are seeking clear, trustworthy insights into how active tracking systems work—and how to subtly redirect, obscure, or reframe their digital traces. This isn’t just niche curiosity; it’s part of a broader shift toward intentional digital identity management, driven by rising awareness of data ethics, surveillance dynamics, and platform limitations. With mobile-first lifestyles dominating U.S. internet use, users are increasingly asking: How can I recognize, respond to, and reshape the invisible tools tracking my digital presence? LBC tracking spoofing has emerged as a fresh, strategic approach—blending technical understanding with practical privacy preservation. This growing curiosity reflects a desire not for shock or taboo, but for clarity, transparency, and effective self-protection in everyday digital interactions. **How Does Watch How LBC Tracking Spoof Exactly Work?** At its core, the LBC tracking spoofing phenomenon refers to techniques and tools designed to disrupt or obscure the digital markers that platforms use to track user behavior. Traditional tracking relies on unique identifiers—cookies, device fingerprints, IP addresses—to build evolving profiles. Spoofing works by either masking these signals or replacing them with decoys that mislead tracking systems without compromising user experience. This approach enables users to reduce unwanted profiling while maintaining access to digital services. The methods vary—from browser extensions that randomize identifiers to browser-integrated privacy modes—but all share a common goal: regaining subtle agency over how personal data flows online. Users uncover practical steps to enable spoofing through trusted privacy tools or custom configuration settings, learning how to detect when tracking is occurring and respond in real time. This blend of education and adaptable solutions turns passive viewers into informed participants in their own digital boundaries.
**Common Questions About Spot and Understand LBC Tracking Spoofing** *How does spoofing stay effective across apps and platforms?* Modern spoofing balances subtlety with adaptability. Tools use real-time signal obfuscation combined with lightweight device authentication to remain undetected by standard tracking scripts, while preserving usability and preventing friction. *Is this only for tech experts or can anyone use it?* No. While foundational concepts involve digital identifiers, modern tools aim for intuitive interfaces—many integrate directly into browsers or privacy-focused apps, making enforcement accessible even to non-technical users. *Does spoofing prevent all tracking, or just limit it?* It significantly reduces the depth and persistence of profiling, especially from behavioral tracking. Complete anonymity online remains elusive, but spoofing levels the playing field by shrinking exploitable footprints. *Can spoofing impact how I use apps or services?* In most cases, it preserves core functionality while lowering invasive data capture. Performance and user experience typically remain unaffected, ensuring practicality across devices. **Opportunities and Practical Considerations** While powerful, tracking spoofing is not a universal fix. Its effectiveness depends on context—platforms vary in detection sophistication, and overuse might trigger friction with service terms. Users should approach it strategically: balance privacy with digital inclusion, stay informed about evolving tracking tactics, and avoid assumptions that spoofing alone eliminates all risk. For businesses and platforms, this trend signals a shift toward ethical design: offering clear controls, transparent data practices, and user-centric identity management is no longer optional—it’s essential for trust and compliance in the US market. **Who Benefits from Understanding Watch How LBC Tracking Spoofs Everything You Think You Know?** This insight matters across diverse audiences: - Privacy-focused individuals seeking empowerment through control - Tech-savvy users aiming to refine digital self-management - Professionals navigating workplace monitoring and identity security - Educators and advocates teaching digital literacy in schools and communities It’s not just about tracking—it’s about cultivating purposeful, informed engagement in a monitored digital world. **Mindful Exploration: A Soft Invitation to Learn** In a space where privacy and trust are increasingly fragile, taking time to understand how tracking works—and how to shape it—offers a meaningful way to participate in your digital life. This isn’t about fear, but about clarity: to make aware choices without anxiety. Whether you’re protecting personal data, improving online efficiency, or just curious, dedicated exploration fosters confidence and control. For a deeper dive into modern tracking mechanisms, spoofing techniques, and privacy best practices, stay informed—knowledge is your first layer of defense. Movements like watching how LBC tracking spoofs expectations aren’t just queries—they’re steps toward a more intentional, empowered digital presence.
**Mindful Exploration: A Soft Invitation to Learn** In a space where privacy and trust are increasingly fragile, taking time to understand how tracking works—and how to shape it—offers a meaningful way to participate in your digital life. This isn’t about fear, but about clarity: to make aware choices without anxiety. Whether you’re protecting personal data, improving online efficiency, or just curious, dedicated exploration fosters confidence and control. For a deeper dive into modern tracking mechanisms, spoofing techniques, and privacy best practices, stay informed—knowledge is your first layer of defense. Movements like watching how LBC tracking spoofs expectations aren’t just queries—they’re steps toward a more intentional, empowered digital presence.
You’re Not Preparing for Zum—This Rewires Your Entire Worldview
You’ll Stop Watching YouTube Forever—This Devastating Fix Works Now!
Stop Paying More Than Necessary—Xfinity Prepaid Unlocks Unexpected Deals